ShaktiCon CTF 2021 - Find me | Forensics
Find me
We found that there was a secret communication between two criminals. Can you find out the secret information?
Downloadable: network2.pcap
Solution
I opened it on Wireshark and checked the TCP stream. There were two meaningful TCP stream.
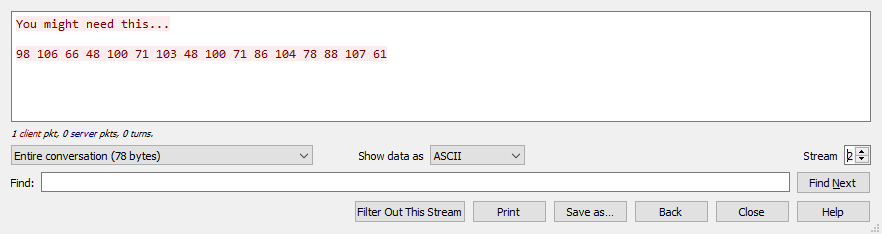
These seem like ASCII code, so I converted them into string and I got a base64 string.
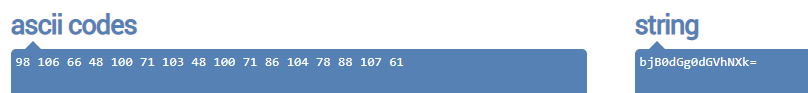
Then, I decoded it and got n0tth4tea5y
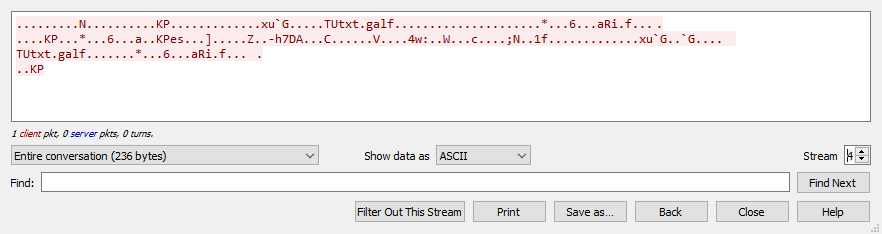
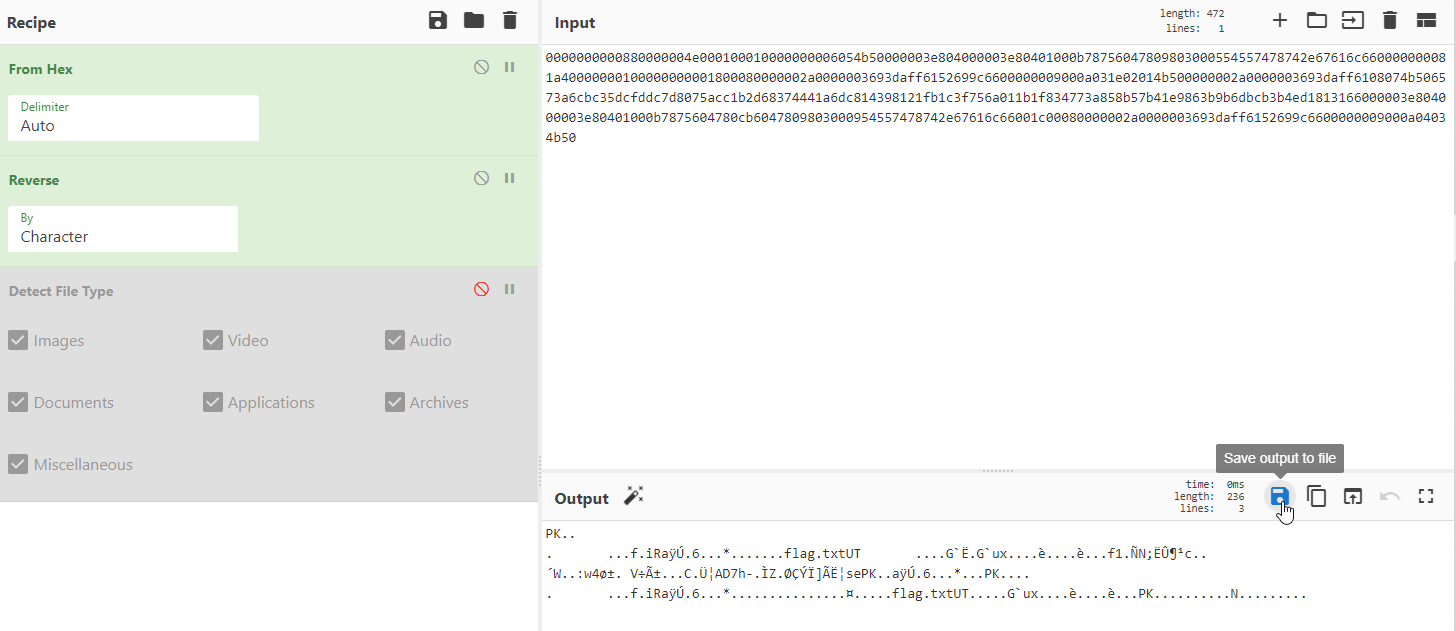
Moving on to the second TCP stream, I see the word “flag.txt” backward in there. So I decided to reverse this on Cyberchef and retrieve it after. To do that, I need to first paste its raw form, which is in hex, on Cyberchef.
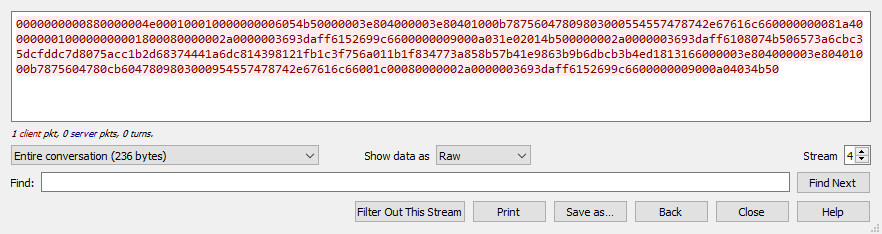
After detecting that the file output is a zip file, I deselected that recipe and save the output to a zip file.
Finally, I used the decoded base64 string as password for the zip file and retrieved the flag: shaktictf{g00d_lUcK_4_tH3_n3xT_cH411eNg3}