UMDCTF 2021 - John's Return | Forensics
John’s Return
I received this network traffic from John, but I don’t what he’s trying to say? Can you figure it out?
Downloadable: received.pcapng
Solution
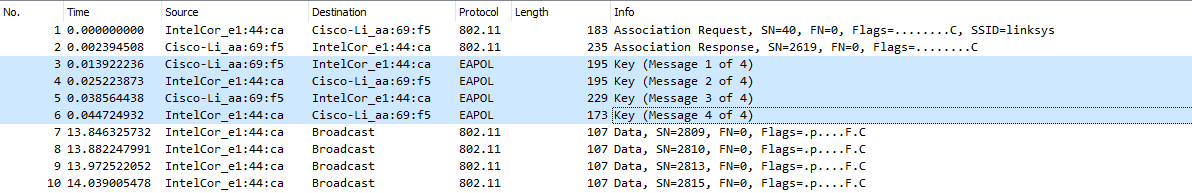
Within the first ten packets, I see that there is the 4 way handshake, which hints that we need to crack the wifi password in order to continue.
I will be using the tool aircrack-ng to crack the password, but I must first convert the file format from pcapng to pcap and I can’t just change the file extension.
I have to use a tool like this: website
//Linux
$aircrack-ng received.s0i0.pcap -w /usr/share/wordlists/rockyou.txt
Reading packets, please wait...
Opening received.s0i0.pcap
Read 76 packets.
# BSSID ESSID Encryption
1 00:23:69:AA:69:F5 linksys WPA (0 handshake, with PMKID)
Choosing first network as target.
Reading packets, please wait...
Opening received.s0i0.pcap
Read 76 packets.
1 potential targets
Aircrack-ng 1.6
[00:00:00] 150/10303727 keys tested (2226.68 k/s)
Time left: 1 hour, 17 minutes, 7 seconds 0.00%
KEY FOUND! [ chocolate ]
Master Key : F8 FA E8 1B 93 20 46 CD F5 7C 0B 7C D0 70 0C 11
F5 70 AD 93 5B 9C 91 97 8D 44 18 70 76 56 5E B6
Transient Key : 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
EAPOL HMAC : 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
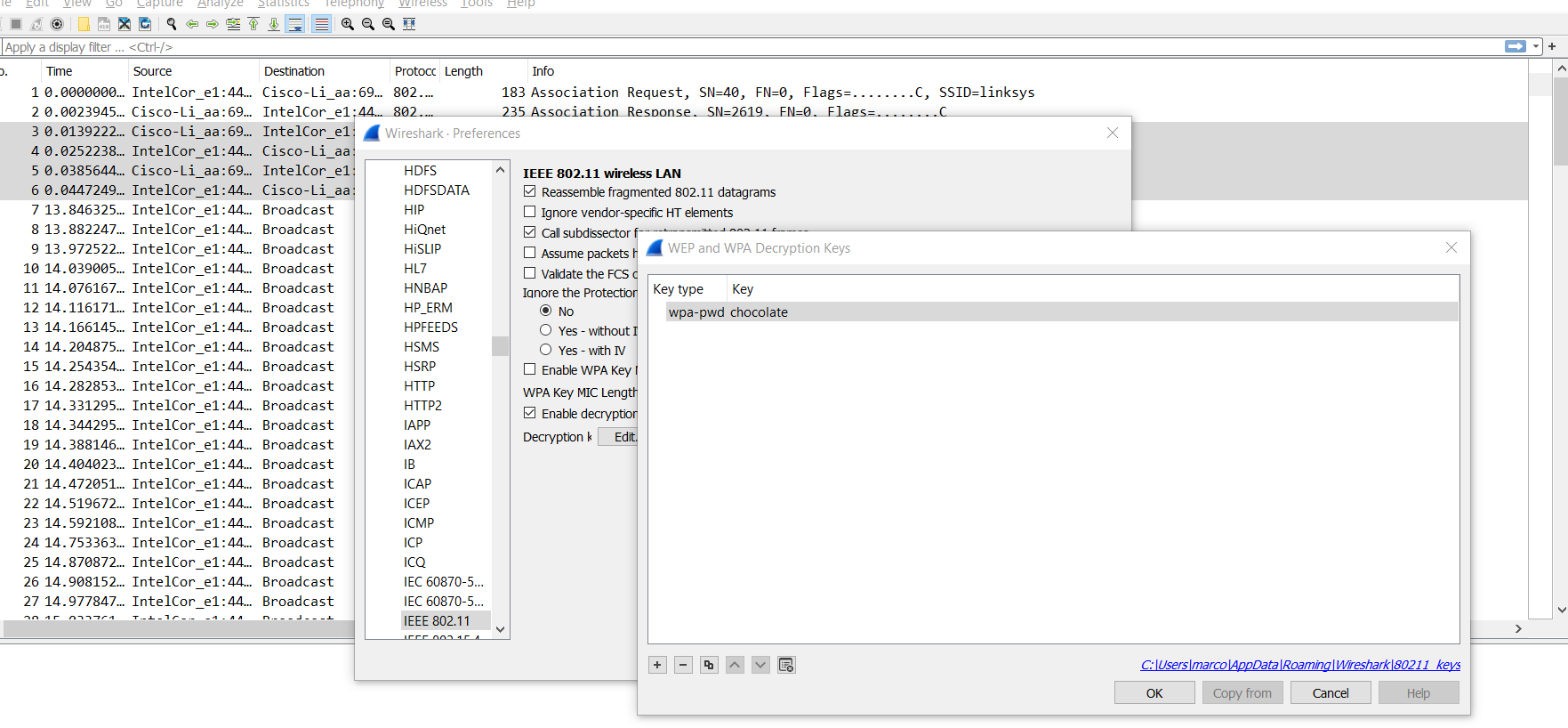
After knowing that the password is chocolate, we will return to Wireshark and put that as the password.
“Edit” > “Preferences” > “Protocols” > “IEEE 802.11 wireless LAN” > “Decryption key Edit” > select “wpa-pwd” and insert “chocolate” as key > press “OK” to see the changes.
This time, there are a bunch of “No valid function found”. However, if we look closely to the data…
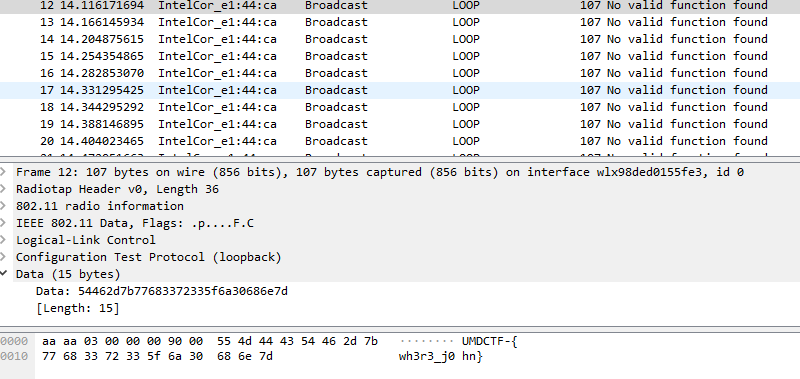
Flag: UMDCTF-{wh3r3_j0 hn}