UMDCTF 2021 - Steg Safari | Steg
Steg Safari
There’s a lot of steps on this safari adventure… come with me to search for wild flags!
Given image:
Solution
The prompt was not lying about having numerous steps in this challenge. This steg challenge was one of the best steg challenges that I have ever done.
I am going to talk about my process step by step.
Step 1: Binwalk the given image (steg_safari.jpg)
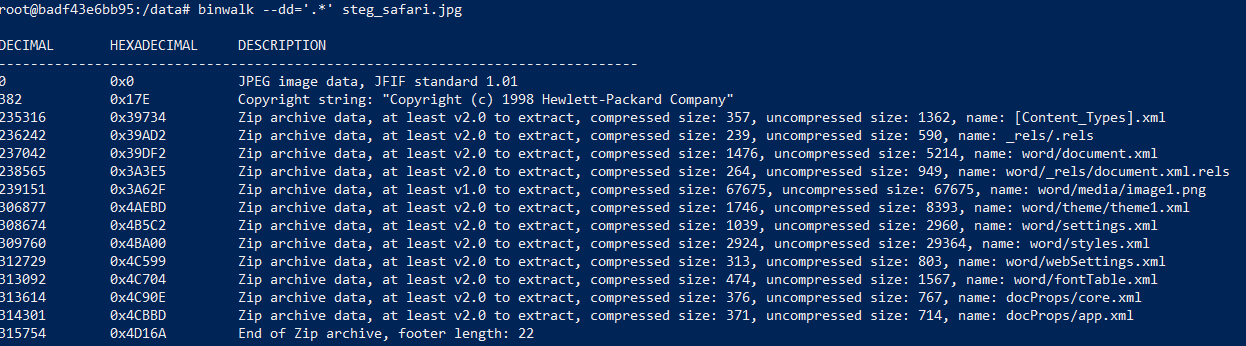
Binwalk should have extracted this folder and within this folder, there are four files, which Binwalk told us that they could be zip files.
Turns out, 39734 was the only zip file that could be opened and here are what’s inside.
Step 2: Explore the extracted folder and find the next clue.
After spending some time exploring, I would like to focus on document.xml within the word folder.
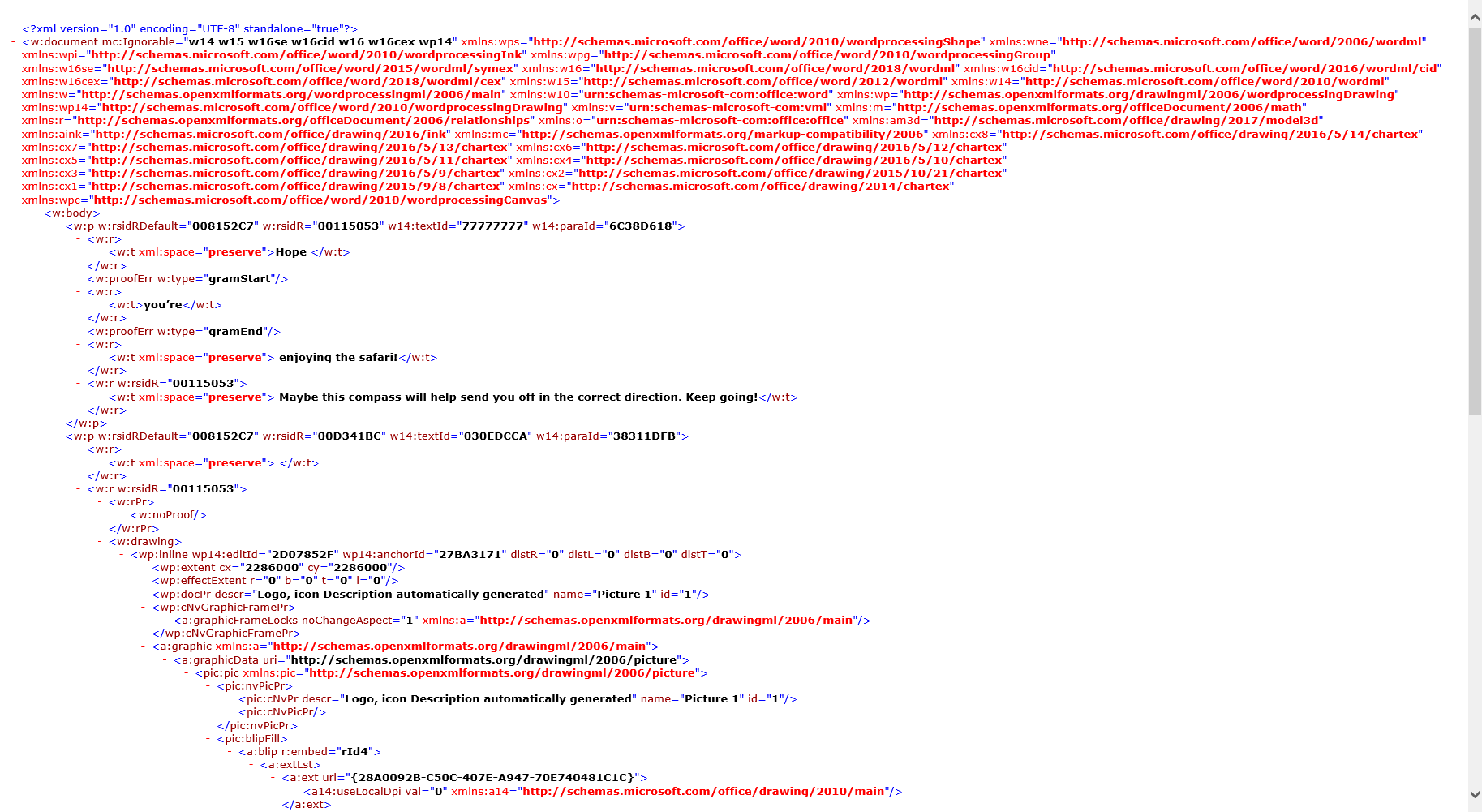
It mentioned that there would be a compass that can help me and I remember seeing a safari image within the media folder.
Step 3: Zsteg the safari icon png
Using Zsteg, I see that there is another png file within and I can extract it using the “b1,rgb,lsb,xy” payload.
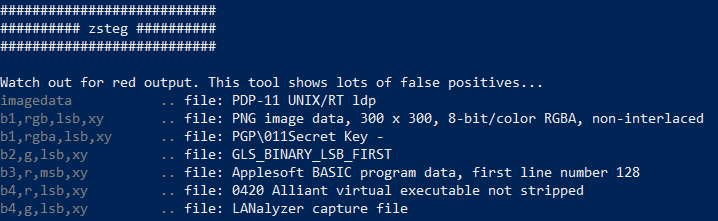
//Command
$zsteg image1.png -E "b1,rgb,lsb,xy" > output.png

Step 4: QR code then Google Drive
I used this QR decoder and the google drive link has an audio file “flag.wav” for me to download.
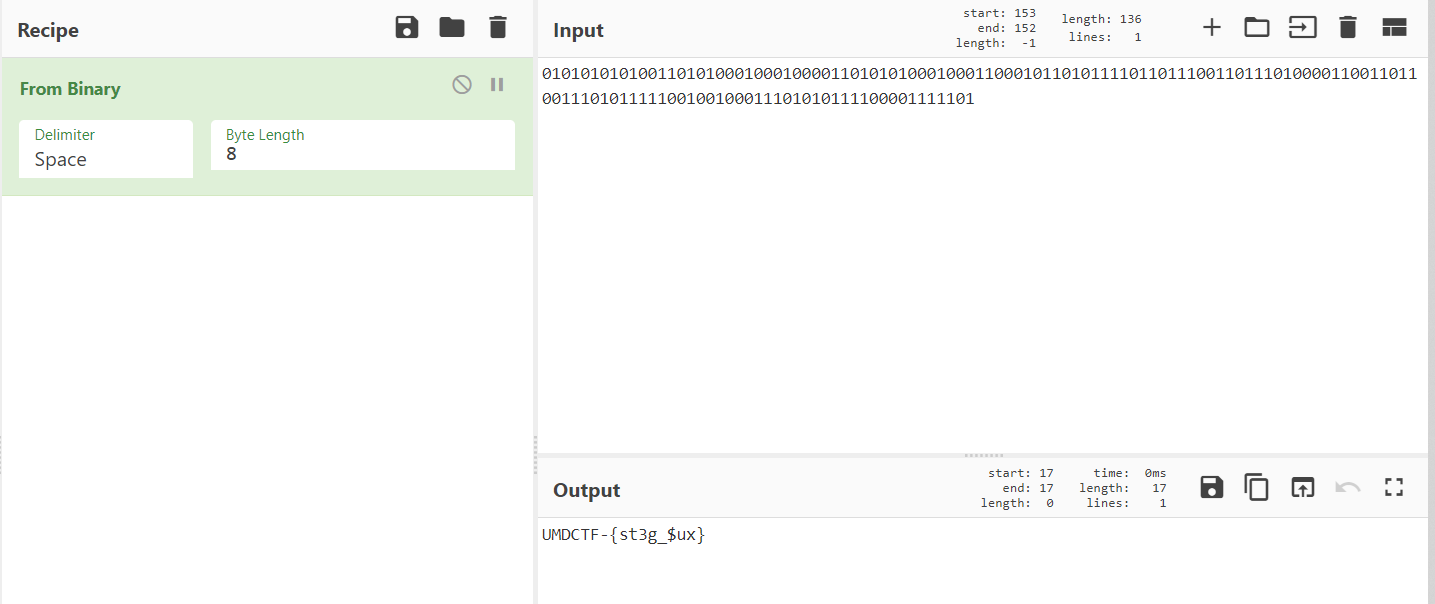
Step 5: Binary
The author pranked us and hinted that there is something interesting happening in the beginning of the audio file.
I used Audacity to open the audio file and I pressed the zoom in button like ten times to see it clearly in waveform.
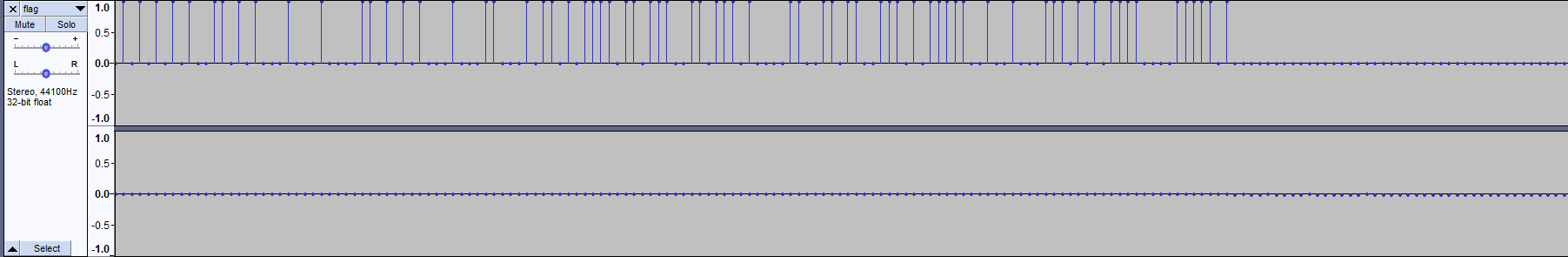
Dot = 0 and Line = 1