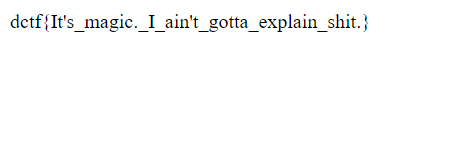dCTF 2021 - Very secure website | Web
Very secure website
Some students have built their most secure website ever. Can you spot their mistake?
http://dctf1-chall-very-secure-site.westeurope.azurecontainer.io/
Solution
Clicking the source code gives the following:
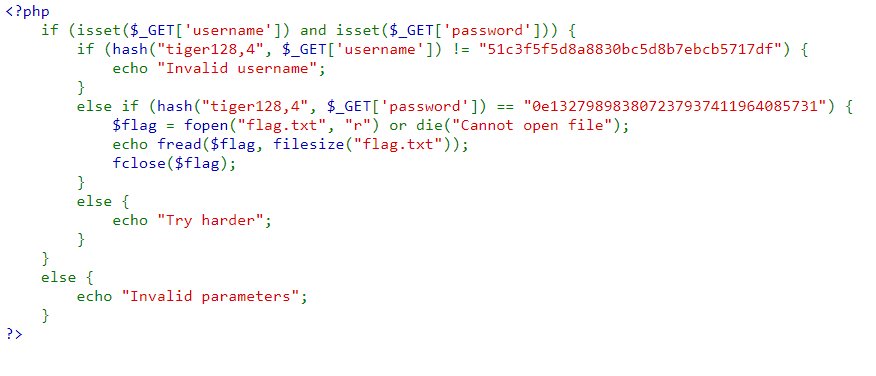
There is php code vulnerability about using the operators “!=” and “==”.
The “51c3f5f5d8a8830bc5d8b7ebcb5717df” hash is easy to figure out. With a simple Google search, it’s revealed to be “admin”. The password requires a bit more research.
Long story short, it turns out I don’t need to find out the identity of the tiger128,4 hash: “0e132798983807237937411964085731”.
I just need to use one of the “magic hashes” which also begin with 0e or 00e and I just need to pass that on as the password.